Going Dark expert group – EU’s surveillance forge

Contents:
· What is #EUGoingDark?
· What are the Pirates doing about this?
· The 42 key points of the secret #EUGoingDark surveillance plan
· The dark work methof of the #EUGoingDark group
· Media reports
· Documents
What is #EUGoingDark?
#EUGoingDark is our label for an EU working group set up by the EU Commission in June 2023. Its official name is the “High Level Group on Access to Data for Effective Law Enforcement” (website, acronym ADELE).
It is co-chaired by the EU Commission and the rotating EU Council Presidency, which are the governments of the EU member states.
Officially, the group is tasked with developing proposals for political strategies and laws on the challenges of digital law enforcement in an open process.
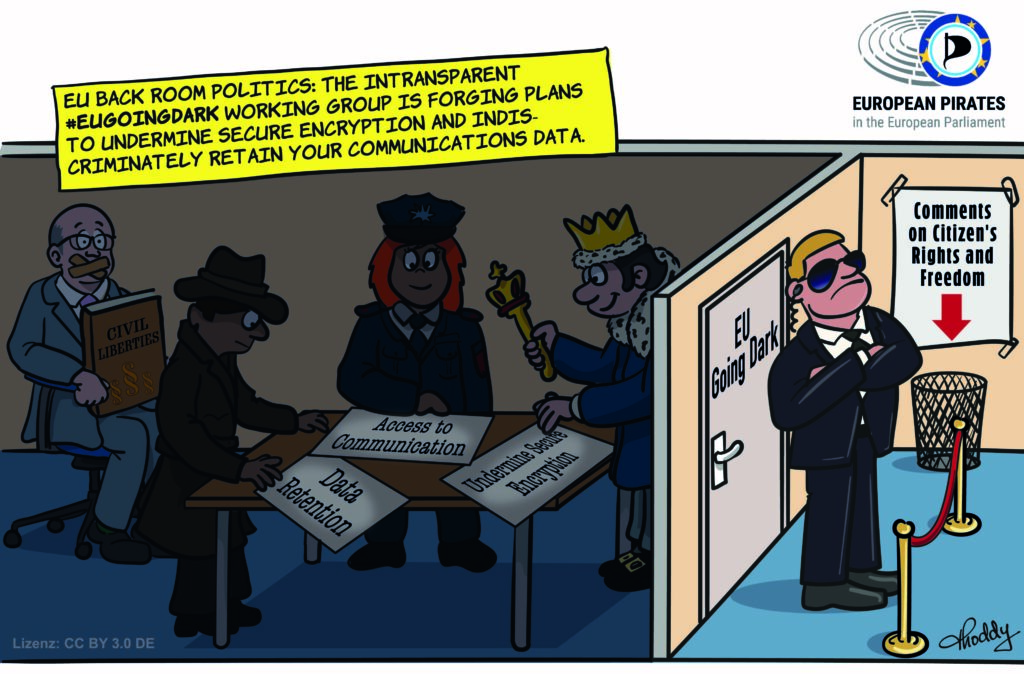
In reality, #EUGoingDark is a non-transparent surveillance forge: police forces and governments ignore civil society and want to reintroduce data retention and undermine encryption without being disturbed.
In short: undemocratic preliminary negotiations are being conducted in the dark, which will serve as a blueprint for future surveillance laws for the next EU Commission.
What are the Pirates doing about this?
We Pirates called for the dissolution of the undemocratic #EUGoingDark group early on. We are fighting for transparency, exchanging ideas with civil society and informing citizens. I have repeatedly requested documents on the meetings of the working group and its subgroups and often had to wait for months only to receive no, few or almost completely redacted documents. What we were able to gather, we have made accessible and analysed: my blog posts on #EUGoingDark. My view is:

“It is clear that undemocratic preliminary negotiations are being conducted here, including on the reintroduction of data retention, against encryption and on the introduction of the “Security by Design” concept, which would be better called “Surveillance by Design”. The group is undemocratic because NGOs and scientists are prevented from participating on an equal footing.”
The 42 key points of the secret #EUGoingDark surveillance plan
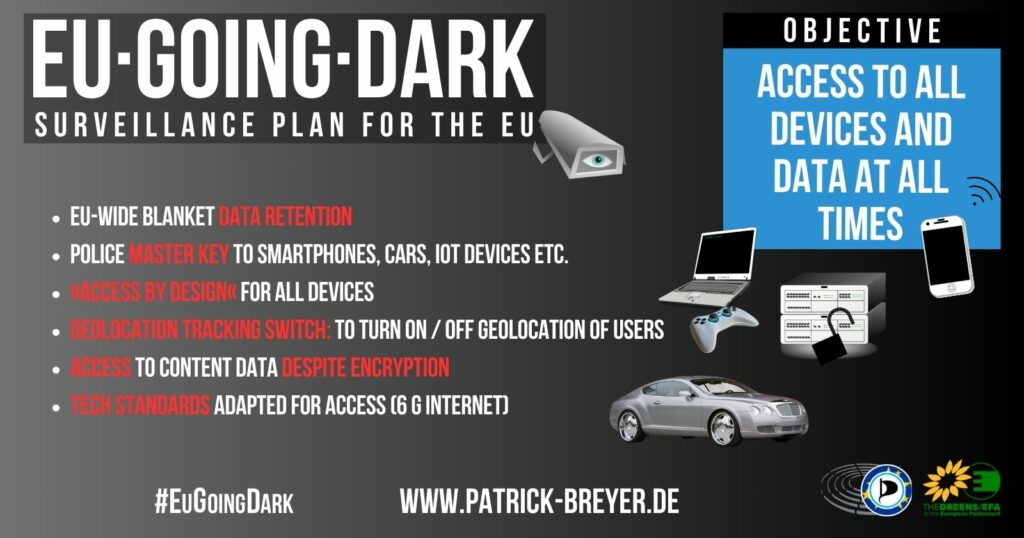
#EUGoingDark has done non-transparent political groundwork for reintroducing blanket retention of communication and location data of all citizens in the EU, and for weakening the encryption of data and communication.
In June 2024, I was finally able to see the confidential 42-point surveillance plan submitted to the new EU Commission as a wish list. It was leaked soon after. On 15 November 2024 the concluding report was published.
Three sub-working groups have drawn up these plans:
Encryption: Law enforcement access to devices

The #EUGoingDark group aims to develop access and monitoring paths to our devices (e.g. smartphones, smart homes, cars) and applications. In doing so, it relies on industry cooperation, influencing technology standardisation committees and standardised access protocols. The group wants to establish the concept of “security by design” in the EU. This means that technology should be developed according to the wishes of police forces and intelligence services and designed to be interceptable from the outset. In short: investigating authorities should be able to gain access to data on all our end devices. Even if the group explicitly denies it, this is about backdoors in one form or another.
Data retention of citizen’s communications metadata

In a landmark judgement, the European Court of Justice overturned the then law on EU-wide data retention of telephone, internet and location data. Many EU governments ignored the judgement and put pressure on the ECJ. Over time, the ECJ has added ever more far-reaching exceptions to the ban on data retention. Instead of protecting citizens’ communications data, the #EUGoingDark group wants to reintroduce blanket mass surveillance. As far as is known, the Belgian model, which is already the subject of legal action, serves as a model.
Encryption: Law enforcement access to data in transit

The third #EUGoingDark sub-working group was also working on plans to undermine encryption. Its focus was on real-time access to data during transmission. Reliable encryption and “privacy preserving architecture[s]” (PDF) are a particular thorn in the side of the working group.
The secretive working methods of the #EUGoingDark group
Why the #EuGoingDark plan must not be the basis for political work
The #EuGoingDark plans were largely forged in secret to the exclusion of digital and fundamental rights organisations. Their agenda and objectives are politically one-sided; criticism is not welcome; solutions that protect fundamental rights and moderate proposals have been ignored. Transparency and collaboration were promised but not delivered.
And more fundamentally, the claim that law enforcement on the internet was increasingly “going dark” is merely a politically motivated myth. Studies show that this assertion is factually incorrect (see, among others: Harvard: “Don’t Panic Making Progress on the “Going Dark” Debate” or Cyber Science Centre Netherlands: “De rol van encryptie in de opsporing“).

Fundamental digital rights muted – surveillance PR instead
The EU Commission is hiding the participants of the #EUGoingDark group meetings. I have requested lists of participants several times, but so far have only received completely redacted documents. (My Toot on Mastodon.) All that is known is that police forces and secret services are represented. Despite the highly sensitive topics in terms of data protection and fundamental rights, the EU Data Protection Supervisor only has the status of an observer. NGOs are not allowed to take part in the group’s meetings. While fundamental rights are muted, the #EUGoingDark group is planning to influence the EU Parliament with targeted surveillance PR.
Politically one-sided preparatory work for new surveillance policies
The outcome of the working group are intended to serve the EU Commission as proposals for political strategies and new legislation. As these proposals were developed in a non-transparent manner from the outset and are one-sided in terms of content and politics, it will be very difficult to introduce alternative proposals that protect fundamental rights into the process in later phases of the political work on these topics.
No equal participation of civil society
Several NGOs and scientists have asked the #EUGoingDark working group to be invited to their working meetings. This did not happen. Instead, they were only invited to a public consultation (EDRi informed about this) but their contributions were not incorporated into the group’s work. Industry representatives, intelligence agencies, police representatives and, as Mullvad VPN reports, at least one former US intelligence officer were allowed to attend the actual meetings.
1st sleight of hand against transparency
The #EUGoingDark working group is blocking serious transparency with sleight of hand and ignorance. According to EU rules (Commission Decision C(2016)3301 PDF), expert groups and their sub-groups must be listed in the “Register of Commission expert groups and other similar bodies” (website). Among other things, the names of individual experts must be listed here. In order to circumvent transparency regulations, the “EU High-Level Expert Group (HLEG) on access to data for effective law enforcement” (PDF) has secretly renamed itself the “High-Level Group (HLG) (…)” (website / archive). Those responsible apparently believe they can use this sleight of hand to ignore EU rules and deceive EU citizens.
2nd sleight of hand against transparency
The #EUGoingDark working group has apparently secretly changed its own Rules of Procedure. The original version of 4 October 2023 (archive PDF) sets out more extensive transparency rules than the later version of 22 January 2024 (website PDF). I am submitting a written question to the EU Commission and requesting a statement (see my request dated 25 April 2024.)
Alternatives and risks are being ignored
As a result of a lack of transparency and a narrow focus, alternative solutions that protect fundamental rights are falling by the wayside. For example, the working group continues to pursue the outdated concept of blanket data retention of all citizens’ communications data, even though there is no evidence of its necessity or benefit (DE blog post). Sensible and urgently needed measures, such as better protection for children (DE blog post and my explanatory video), play no role in #EUGoingDark. At the same time, the working group ignores the dangers of indiscriminate mass surveillance to the fundamental rights and freedoms of EU citizens.
Media reports
- 26.06.2024: Glyn Moody / techdirt.com: EU’s ‘Going Dark’ Expert Group Publishes 42-Point Surveillance Plan For Access To All Devices And Data At All Times 🇬🇧
- 20.06.2024: nd: Chatkontrolle: Verschlüsselung bleibt in der EU vorerst sicher – EU-Abstimmung zu »kundenseitiger« Überwachungstechnik vertagt, Ball liegt nun bei Ungarn 🇩🇪
- 13.06.2024: EDRi: High-Level Group “Going Dark” outcome: A mission failure 🇬🇧
- 12.06.2024: The Fifth Skill News: EU anti-encryption crusaders seek to turn your digital devices into spyware 🇬🇧
- 10.06.2024: netzpolitik.org: Going Dark: EU-Staaten wollen Zugriff auf verschlüsselte Daten und mehr Überwachung 🇩🇪 – English version of that article: EU States Push for Access to Encrypted Data and Increased Surveillance 🇬🇧
- 06.06.2024: statewatch.org: Policing by design: the latest EU surveillance plan 🇬🇧
- 04.06.2024: netzpolitik.de: Going Dark: EU-Expertengruppe fordert Hintertüren und mehr Überwachung 🇩🇪
- 04.06.2024: t-online.de: Internes Dokument von EU-ExpertengruppeDie EU will WhatsApp-Chats mitlesen 🇩🇪
- 04.06.2024: Heise.de: Verschlüsselung: Polizei will in Echtzeit an Datenströme von WhatsApp & Co. 🇩🇪
- 21.05.2024: Mullvad VPN: Going Dark: The war on encryption is on the rise. Through a shady collaboration between the US and the EU.« 🇬🇧
- 16.01.2024: netzpolitik.org: “Going Dark” mal anders: Zivilgesellschaft bleibt im Dunkeln bei EU-Beratungen zu Verschlüsselung 🇩🇪
- 15.01.2024: Heise.de: Crypto Wars: Bürgerrechtler wollen Licht in “Going Dark”-Arbeitsgruppe bringen 🇩🇪
- 11.12.2023: netzpolitik.org: EU berät über “Going Dark”: Hinter verschlossenen Türen 🇩🇪
- 28.03.2023: Euractiv: EU countries in search of ‘solutions’ over data retention, encryption 🇬🇧
Timeline
- 6 June 2023: Commision decision “setting up a high-level group on access to data for effective lawenforcement”
- Between June 2023 and June 2024: Four meetings of the #EuGoingDark group and its sub-groups, partly documented on the group’s website
- 6 June 2024: Publication of the 42 recommendations of the #EuGoingDark group
- 1 July 2024: Start of the Hungarian Presidency, announcing to continue the #EuGoingDark- program („European consensus on the retention and access to law enforcementdata“)
- Announced for Q2 2024: Second Eurojust Data Retention Report
- 16 July 2024: Constituent Meeting of the European Parliament
- 3-5 September: Working Party on Cooperation in Criminal Matters (COPEN)
- Date tba: State of the Union speech by the President of the European Commission
- Date tba: Adoption of the Commission work programme 2025
- 10-11 October 2024: Justice and Home Affairs Council
- 16-17 October: EU -U.S. Senior Officials Meeting on Justice and Home Affairs
- 15 November: Final meeting of the #EuGoingDark group and release of concluding report
- 25 November: Safe in Europe Forum 2024
- 27 November: Concluding report of the #EuGoingDark recommendations to be presented to the Working Party on Cooperation in Criminal Matters (COPEN)
- Date tba: Joint priorities of the EU institutions for 2025
- 9-11 December 2024: 140th Management Board Meeting of Europol
- 12-13 December 2024: Justice and Home Affairs Council with “exchange of views on Access to data for effective law enforcement”
- 1 January 2025: Beginning of the Polish Council Presidency

Documents
- 15/11/2024: Concluding report (PDF)
- 04/11/2024: Comments by European Data Protection Board (EDPB) (PDF)
- 12/09/2024: State of play and envisaged next steps (PDF)
- 30/05/2024: Currently important: Secret minutes of a meeting of an EU committee of EU member states (published on netzpolitik.org)
- 22/05/2024: Currently important: »Recommendations from the High-Level Group on Access to Data for Effective Law Enforcement« (PDF on netzpolitik.org) My statement on this.
- 13/04/2023: »Scoping paper for the High-Level Expert Group on access to data for effective law enforcement « (PDF)
- 06/06/2023: »Commission decision: Setting up a high-level group on access to data for effective law enforcement« (PDF)
Documents obtained by my Freedom of Information request »Documents of the HLG on access to data for effective law enforcement and of its sub-groups«, received on 28.05.2024:
- Doc. 1: Going Dark Flash Report, 17 January 2024 – not disclosed
- Doc. 2: Data Retention: The Belgian Experience | “Thanks to this « Narrative » decision was made to repair again the Belgian law”
- Doc. 3: CJEU Requirements on Data Retention
- Doc. 4: Proximus – Operator perspective on the new Belgian data retention framework
- Doc. 5: Presentation by ETSI
- Doc. 6: Swedish providers response to geographically targeted retention – not disclosed
- Doc. 7: Going Dark Flash Report, 13 February 2024 – not disclosed
- Doc. 8: Presentation by the Belgian Police on real-time access to data stored on devices | front door approach
- Doc. 9: LEON: Ways forward – not disclosed
- Doc. 10: Europol’s presentation | Home Routing, SMS interceptoin challenges
- Doc. 11: Admissibility of evidence from the receiving state’s perspective | “it seems essential to provide for regulation of encrypted communication services through the updating of Electronic Communications Codes”
- Doc. 12: ETCI TC Cyber | “Provide on-line on the fly real time interception of OTT E2E communications”
- Doc. 13: EU Science Hub | “Vulnerability management for Internal Security”
- Doc. 14: Public Prosecution Service NL | “Real time interception and ECS in practice”, wiretapping of ECS vs ICS vs ISP, Microsoft Netherlands Kooperation
- Doc. 15: EDRI | Note: „EDRi’s written contribution does not amount to a tacit agreement with the objectives of the HLG. What it does instead is to point to the narrow political agenda of the HLG which focuses on law enforcement interests solely. In particular, how law enforcement can get more access to data, without proper regard for the fundamental rights implications of the suggested solutions.“
- Doc. 16: EACDTA | “Privacy concerns people, not machines. Machines, programs, have no consciousness and are therefore privacy agnostic.”, “llegal content detection technology”
- Doc. 17: Going Dark Flash Report, 1 March 2024 – not disclosed
- Doc. 18: French Ministry of the Interior | “Weapons systems: Pre-commercial procurement”
- Doc. 19: ILNAS Luxembourg | New paradigm in the European standardization ecosystem – European Standardisation Strategy (COM(2022) 31)
- Doc. 20: COM on the Access to Date stored on devices | “Increase and coordinate the EU effort to engage with identified relevant standardisation bodies.”, “Handbook outlining how to engage with industry to gain insight into the legal processes to gain access to data stored in users’ devices.”, “Legislation for tackling the use of encryption devices which have been proven to be solely used for the purpose of communication between criminal actors.”, “Set obligations for technology providers to facilitate access to data at rest in user’s devices when requested by judicial authorities, for example by providing technical assistance.”
- Doc. 21: COM presentation on data retention| “address open challenges such as non-unique IP addresses lack of geolocation or encryption”, “create a level playing field for all electronic communication service providers, including OTTs.”, “Foster Member States’ involvement in setting up standardised formats for data retention and access, based on ETSI standards (notably for categories of data currently not covered by standards).”
